IoT VPC AWS Not Working? Fix Your Remote Connection Now!
The reason why securely connecting remote IoT devices to an AWS VPC might not work, especially on Windows, can be multifaceted, often a combination of factors. This is a common challenge faced by developers, IT professionals, and IoT enthusiasts who rely on AWS for their cloud infrastructure. So, you’re trying to securely connect your remote IoT devices to an AWS VPC, but it’s not working? Yeah, we’ve all been there.
Whether you’re troubleshooting connectivity issues or setting up a new environment, this problem can be a real pain in the neck. However, the seemingly simple act of securely connecting remote IoT devices to an AWS Virtual Private Cloud (VPC) can quickly become a complex maze of configurations, security settings, and troubleshooting steps, especially when working on a Windows environment. But don’t worry, because today we’re diving deep into why this happens and how to fix it. This isn't just another tech guide; it's your ultimate resource to getting things up and running.
Table of Contents
- Understanding the Core Challenge: Securely Connecting Remote IoT to AWS VPC
- The Usual Suspects: Common Causes for Connection Failure
- A Systematic Approach to Troubleshooting
- Deep Dive into AWS VPC Configuration Best Practices
- Securing Your IoT Devices: Beyond Connectivity
- Practical Steps for Resolving "Securely Connect RemoteIoT VPC AWS Not Working" on Windows
- Case Study: Raspberry Pi and AWS VPC Connectivity
- Maintaining a Secure and Efficient IoT Environment
Understanding the Core Challenge: Securely Connecting Remote IoT to AWS VPC
The phrase "securely connect remoteiot vpc aws not working" encapsulates a common issue that many AWS users encounter, and understanding the root causes and solutions is crucial. When you aim to connect remote IoT devices, such as sensors, actuators, or even single-board computers like a Raspberry Pi, to your AWS Virtual Private Cloud (VPC), you're essentially creating a secure tunnel for data exchange and remote management. This setup is fundamental for many modern IoT applications, offering enhanced security, dedicated network space, and seamless integration with other AWS services.
However, the journey isn't always smooth. When encountering issues like "securely connect remoteiot vpc aws not working," the root cause often lies in misconfigurations, network conflicts, or overlooked security settings. This isn't just about getting a ping response; it's about establishing a robust, encrypted, and authorized connection that can handle continuous data streams and remote commands without exposing your devices or your cloud infrastructure to unnecessary risks. Addressing the issue of securely connecting remote IoT devices to a VPC on AWS involves a multifaceted approach. It requires a deep understanding of networking principles, security protocols, and the unique configurations of AWS services. This article is here to help you sort through those moments of confusion.
The Usual Suspects: Common Causes for Connection Failure
When the connection isn't working as expected, it can be due to a variety of factors. These problems can arise due to incorrect VPC peering, incorrect IAM roles, or firewall restrictions. We will go through the usual suspects behind why your setup for "securely connect remoteiot vpc aws" might not be working on Windows, and we'll give you some clear steps to get things running properly.
Misconfigured Security Groups and Network ACLs
Security Groups (SGs) act as virtual firewalls for your instances and network interfaces, controlling inbound and outbound traffic. Network Access Control Lists (NACLs) operate at the subnet level, providing another layer of stateless packet filtering. Misconfigurations here are incredibly common and often the first place to look when you can't securely connect remote IoT VPC to AWS.
- How Much Does Jimmy Kimmel Make A Year
- Lecy Goranson
- Chloe Bennet
- How Old Is Sean Penn
- Secret Therapy Leaks
- Incorrect Ingress/Egress Rules: Your IoT device needs to be able to send data into your VPC (ingress) and potentially receive commands from it (egress). If the necessary ports (e.g., MQTT on 8883 for secure connections, or SSH on 22 for management) are not open in both directions, communication will fail.
- Source IP Restrictions: You might have restricted access to specific IP ranges. If your remote IoT device's public IP changes or is not within the allowed range, it will be blocked. For devices behind NAT, this can be particularly tricky.
- NACL Deny Rules: While less granular than SGs, a restrictive NACL rule can override an otherwise permissive Security Group, blocking traffic at the subnet level. Remember, NACLs are stateless, meaning you need rules for both inbound and outbound traffic.
Incorrect Routing Tables and Subnet Associations
Routing tables dictate how network traffic is directed within your VPC and to external networks. If your IoT device's traffic isn't routed correctly, it simply won't reach its destination in your AWS VPC.
- Missing or Incorrect Routes: For your remote IoT device to reach a service within your VPC (e.g., an EC2 instance, an RDS database, or an IoT Core endpoint), there must be a route that directs traffic from the internet gateway (or VPN/Direct Connect) to the correct subnet.
- Subnet Association Issues: Ensure that the subnet where your target resources reside is correctly associated with the routing table that contains the necessary routes for incoming IoT traffic.
- Overlapping CIDR Blocks: If your on-premise network (where the IoT device resides) has IP address ranges that overlap with your AWS VPC's CIDR block, routing conflicts will occur, preventing communication.
IAM Role and Policy Permissions Deficiencies
AWS Identity and Access Management (IAM) is crucial for controlling who (or what) can access your AWS resources. For IoT devices, this means granting them the necessary permissions to publish data to IoT Core, subscribe to topics, or interact with other AWS services.
- Insufficient IoT Core Policies: Devices need specific permissions to connect to AWS IoT Core, publish messages, and subscribe to topics. If the attached IAM policy or IoT policy is too restrictive, the device won't be able to authenticate or exchange data.
- Incorrect Device Certificates/Credentials: For secure connections (e.g., using TLS/SSL), devices must present valid certificates or credentials. Expired, revoked, or incorrectly configured certificates will lead to connection failures.
- Role Trust Policies: If you're using IAM roles for your devices (e.g., through AWS IoT Greengrass or a custom credential provider), ensure the trust policy allows the device to assume that role.
On-Premise Firewall and Network Restrictions (Windows Specific)
While AWS configurations are critical, the problem often originates closer to the device, especially when operating on a Windows environment.
- Windows Firewall: The default Windows Firewall can block outbound connections from your IoT device or the machine hosting your IoT gateway software. Ensure that rules are in place to allow traffic on the necessary ports (e.g., 8883 for MQTT, 443 for HTTPS).
- Corporate Proxies/VPNs: If your Windows environment is behind a corporate proxy or VPN, it might be intercepting or blocking traffic to AWS endpoints. You may need to configure proxy settings for your IoT application or whitelist AWS domains.
- Antivirus/Endpoint Protection: Some security software can interfere with network connections, mistaking legitimate IoT traffic for malicious activity. Temporarily disabling it (for testing only, with caution) can help diagnose if it's the culprit.
A Systematic Approach to Troubleshooting
Tackling the "securely connect remoteiot vpc aws not working on windows" problem can seem complex, but with a systematic approach and the right knowledge, it's entirely manageable. To resolve the problem, a comprehensive approach is crucial, which includes identifying the underlying issue and methodically testing each potential point of failure. Don't jump to conclusions; start with the basics and work your way up the network stack.
- Verify Basic Network Connectivity: Can your device ping public AWS endpoints (e.g.,
ping aws.amazon.com)? This confirms basic internet access. Usetracert(on Windows) to trace the path and identify where traffic might be dropping. - Check Device Logs: Your IoT device's application logs are invaluable. They often contain error messages related to connection attempts, authentication failures, or certificate issues.
- AWS CloudWatch Logs: If your IoT Core rules or Lambda functions are involved, check CloudWatch logs for any errors or indications of traffic being received or dropped.
- AWS Network Reachability Analyzer: This powerful tool in the AWS console can help you diagnose network connectivity issues between resources within your VPC or from your VPC to external endpoints. It simulates network paths and identifies blocking security groups, NACLs, or routing issues.
- Test with Simplified Configurations (Cautiously): For diagnostic purposes only, you might temporarily relax certain security rules (e.g., open a Security Group to 0.0.0.0/0 for a specific port) to see if connectivity is established. IMMEDIATELY revert these changes once testing is done to maintain security.
Deep Dive into AWS VPC Configuration Best Practices
A comprehensive guide to securely connecting remote IoT VPC on AWS must emphasize foundational best practices. Many issues with "securely connect remoteiot vpc aws not working" stem from deviations from these principles during initial setup. By adhering to these, you lay a solid groundwork for reliable and secure IoT operations.
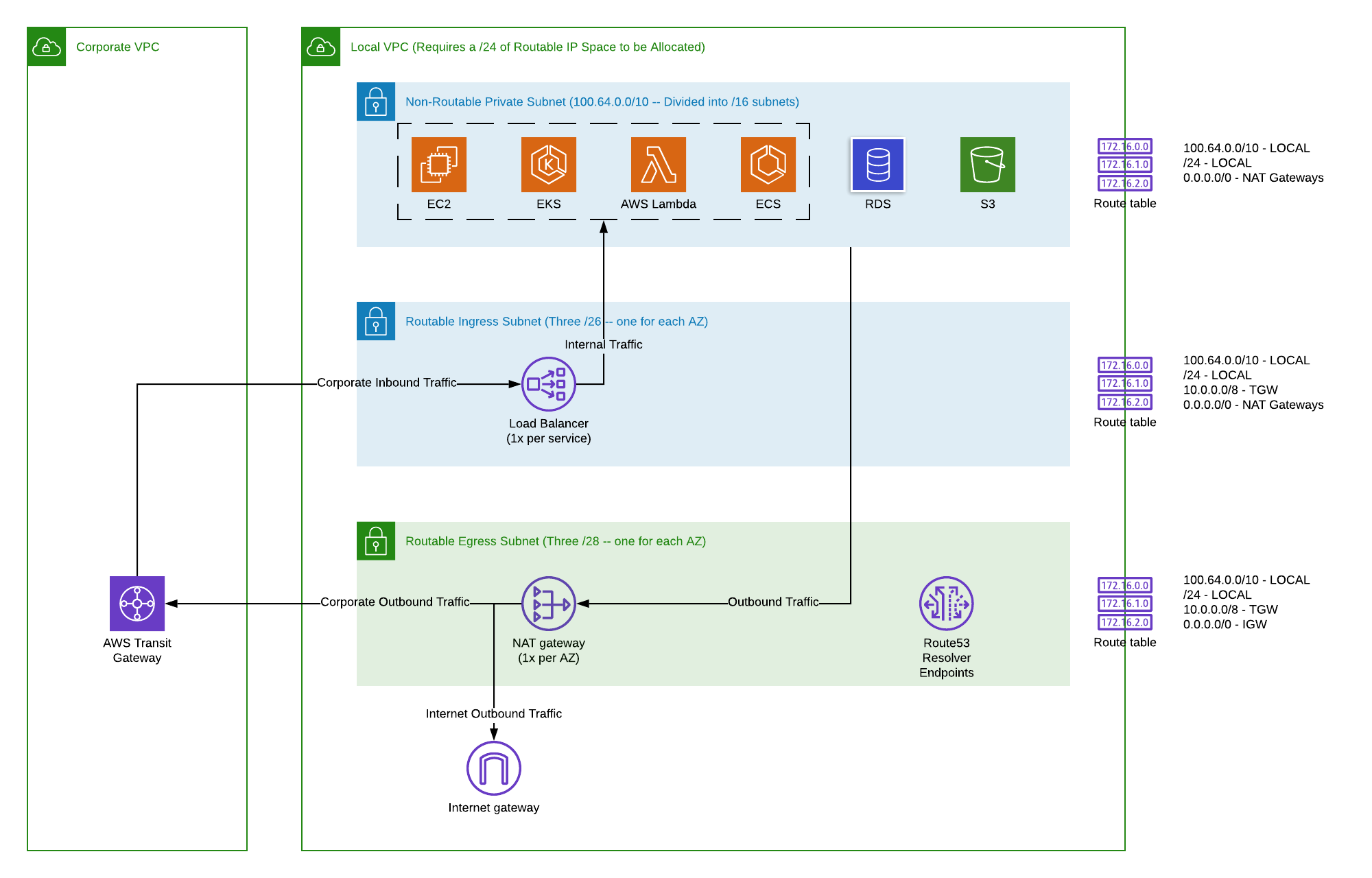
VPC Peering and Transit Gateway Considerations
When your IoT devices need to interact with resources across multiple VPCs, understanding how to connect these networks is critical.
- VPC Peering: This allows you to connect two VPCs directly, enabling instances in either VPC to communicate as if they are within the same network. Ensure your peering connection is active, and crucially, that routing tables in both VPCs have explicit routes pointing to the peer VPC's CIDR block. Also, remember that security groups and NACLs still apply across peered connections.
- AWS Transit Gateway: For more complex network topologies involving many VPCs, on-premise networks, and VPNs, a Transit Gateway acts as a central hub. It simplifies network management by allowing you to connect thousands of VPCs and on-premises networks to a single gateway. If your IoT devices are connecting via a VPN to a Transit Gateway, ensure the correct attachments and routes are configured on the Transit Gateway route table.
Ensuring Proper Endpoint Configuration (VPC Endpoints, IoT Core Endpoints)
To securely connect remote IoT devices to AWS VPC, you often leverage AWS IoT Core, which has its own set of endpoints. For private connectivity to other AWS services within your VPC, VPC Endpoints are essential.
- AWS IoT Core Endpoints: Your IoT devices connect to specific AWS IoT Core data and credential endpoints. These are region-specific. Ensure your device client is configured with the correct endpoint URL (e.g.,
a1b2c3d4e5f6.iot.us-east-1.amazonaws.com). For private connectivity, AWS IoT Core supports VPC endpoints, allowing devices within your VPC to connect to IoT Core without traversing the public internet. - VPC Endpoints (Interface and Gateway):
- Interface Endpoints (Powered by AWS PrivateLink): These allow you to privately access AWS services (like IoT Core, S3, DynamoDB, Lambda) from within your VPC without using an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. This significantly enhances security and reduces data transfer costs. Ensure the security group associated with your interface endpoint allows inbound traffic from your IoT devices' subnets on the necessary ports.
- Gateway Endpoints: Specifically for S3 and DynamoDB, these provide a reliable connection to these services from within your VPC. While less common for direct IoT device connectivity, they are vital if your IoT application relies on these services for data storage or processing.
Securing Your IoT Devices: Beyond Connectivity
The "securely" in "securely connect remoteiot vpc aws not working" is paramount. It's not just about getting data through; it's about protecting that data and your devices from unauthorized access and malicious attacks. This involves a multi-layered security approach.
- Device Identity and Authentication: Every IoT device should have a unique identity. AWS IoT Core uses X.509 certificates for device authentication, ensuring that only trusted devices can connect. Implement robust certificate management, including rotation and revocation processes.
- Principle of Least Privilege: Grant your IoT devices only the minimum necessary permissions (IAM policies) to perform their intended functions. Avoid using overly permissive policies.
- Data Encryption: Ensure data is encrypted in transit (using TLS/SSL for MQTT, HTTPS) and at rest (for data stored in S3, DynamoDB, etc.).
- Secure Device Provisioning: Implement secure provisioning methods to ensure devices are authenticated and configured correctly from the moment they are deployed.
- Secure Remote Management: For Raspberry Pi users, SSH is an invaluable tool for remote IoT management, enabling them to execute commands, transfer files, and configure settings without physical access. This guide will walk you through everything you need to know about securely connecting to your Raspberry Pi using remoteiot P2P SSH, including the download process. P2P SSH provides a direct, encrypted tunnel, bypassing the need for complex firewall rules or public IP addresses on the device side, making it an excellent solution when "securely connect remoteiot vpc aws not working" due to local network constraints.
- Regular Security Audits: Periodically review your security configurations, device logs, and access patterns to identify and mitigate potential vulnerabilities.
Practical Steps for Resolving "Securely Connect RemoteIoT VPC AWS Not Working" on Windows
When you're facing the dreaded "securely connect remoteiot vpc aws not working windows" issue, a hands-on approach is needed. Here are actionable steps you can take to diagnose and fix the problem:
- 1. Verify Device Client Configuration:
- Endpoint URL: Double-check that your IoT device client (e.g., MQTT client, SDK) is configured with the correct AWS IoT Core data endpoint for your region.
- Certificates/Keys: Ensure the device has the correct client certificate, private key, and the AWS root CA certificate. Verify their paths and permissions. A common mistake is using the wrong private key or an expired certificate.
- Topic Permissions: Confirm that the IoT policy attached to your device's certificate grants permission to publish/subscribe to the specific MQTT topics it's trying to use.
- 2. Inspect AWS IoT Core Metrics and Logs:
- Go to the AWS IoT Core console. Check "Monitor" > "Metrics" for connection attempts, successful connections, and rejected connections. This provides a high-level overview.
- Enable CloudWatch Logs for AWS IoT Core. Look for "Connect" and "Disconnect" events, and any "Rejected" messages, which often provide specific reasons for connection failures (e.g., "CLIENT_ERROR: Certificate not found").
- 3. Review VPC Security Groups and NACLs:
- Target Security Group: Identify the security group attached to the resource your IoT device is trying to reach (e.g., an EC2 instance, a VPC endpoint). Ensure it has an inbound rule allowing traffic on the necessary port (e.g., 8883 for secure MQTT, 22 for SSH) from the source IP range of your IoT device or your network.
- Subnet NACL: Check the NACL associated with the subnet. Remember, NACLs are stateless. You need both inbound and outbound rules for the relevant ports. For example, if allowing inbound 8883, you also need outbound ephemeral ports (1024-65535) for the return traffic.
- 4. Check VPC Route Tables:
- Ensure the subnet where your target resource resides has a route to the internet gateway (for public IoT Core endpoints) or to the VPC endpoint (for private connectivity).
- If using VPC peering or Transit Gateway, verify that routes exist for traffic to flow between the networks.
- 5. Diagnose On-Premise (Windows) Network:
- Windows Firewall: Temporarily disable Windows Firewall on the machine hosting the IoT device or gateway (for testing only!). If this resolves the issue, re-enable it and create specific inbound/outbound rules for your IoT application.
- Proxy/VPN Settings: If your Windows environment uses a proxy server, ensure your IoT client is configured to use it, or that the proxy allows traffic to AWS IoT Core endpoints. If using a VPN, confirm it's not blocking or misrouting traffic.
- Network Tools: Use
netstat -anto see active connections and listening ports. Usetelnet your-iot-endpoint.amazonaws.com 8883(or the relevant port) from your Windows machine to test if a TCP connection can be established. A successful connection indicates that local firewalls and basic routing are likely okay.
- 6. IAM Policy Review:
- Go to AWS IAM. Find the IoT policy attached to your device's certificate. Verify that it has
iot:Connect,iot:Publish,iot:Subscribe, andiot:Receivepermissions on the correct resources (e.g.,arn:aws:iot:your-region:your-account-id:client/${iot:ClientId}or specific topic ARNs).
- Go to AWS IAM. Find the IoT policy attached to your device's certificate. Verify that it has
Case Study: Raspberry Pi and AWS VPC Connectivity
Connecting your Raspberry Pi to a remote IoT Virtual Private Cloud (VPC) on Amazon Web Services (AWS) is a powerful way to securely manage IoT devices. Raspberry Pis are popular choices for IoT prototyping and deployment due to their versatility and low cost. However, they often encounter the "securely connect remoteiot vpc aws not working" problem, especially when the development environment is Windows-based.
Common issues specific to Raspberry Pi include:
- Incorrect Clock Synchronization: TLS/SSL connections are highly sensitive to time synchronization. If your Raspberry Pi's clock is significantly out of sync with AWS servers, certificate validation will fail. Ensure NTP is configured on your Pi.
- Power Supply Issues: An unstable power supply can lead to intermittent network connectivity or unexpected reboots, disrupting persistent connections.
- SD Card Corruption: Frequent power cycles or improper shutdowns can corrupt the SD card, leading to file system errors that prevent the IoT client from starting or accessing its certificates.
- Python/Node.js SDK Dependencies: Ensure all required libraries and dependencies for your chosen AWS IoT SDK (e.g., Paho MQTT, AWS IoT Device SDK for Python) are correctly installed and up to date on the Raspberry Pi.
For remote management, remember that this guide will walk you through everything you need to know about securely connecting to your Raspberry Pi using remoteiot P2P SSH, including the download process. This method can circumvent many local network and firewall issues that contribute to the "securely connect remoteiot vpc aws not working" scenario, providing a direct, secure tunnel for troubleshooting and configuration.
- Juice Wrld Police Report
- Shyna Khatri Web Series Online
- How Much Does Jimmy Kimmel Make A Year
- Trump Fecal Incontinence
- Kathryn Mae Wiki

How To Fix Securely Connect Remote IoT VPC AWS Not Working: A
AWS VPC Subnets, Routing Tables And Internet Access Using, 56% OFF

Securely Connect Remote IoT VPC Raspberry Pi AWS Free: A Comprehensive